Michigan, US, sixteenth August 2024, ZEX PR WIRE, Guided Hacking is happy to announce the launch of its new Binary Exploit Improvement Course, aimed toward breaking down the complicated ideas behind binary exploitation and bringing this craft to a bigger viewers. This in-depth course is designed to take learners from foundational ideas to superior strategies in exploit growth, beginning with the important matter of buffer overflows but in addition going over sophisticated duties like bypassing safety features and fuzzing for brand spanking new bugs.
Linux Buffer Overflow – Exploit Improvement 9
(a teaser of chapter 9 of the course)
Beginning with a Easy Buffer Overflow
The journey begins with an in-depth rationalization of exploiting easy buffer overflows utilizing VulnServer. This foundational chapter, out there since September 3, 2022, guides college students by reversing the VulnServer software utilizing IDA Free, a well-liked disassembler. Members will discover ways to exploit a direct RET overwrite, a elementary method in binary exploitation. By the tip of this chapter, you can be outfitted to overwrite the return deal with throughout runtime, redirecting execution circulate to their customized shellcode. This turns into the muse of the course, with every chapter constructing upon this primary method & adapting it to numerous more and more troublesome conditions.
Course Overview
Guided Hacking’s Exploit Improvement Course is meticulously structured to offer a step-by-step studying expertise. Every module builds upon the earlier one, guaranteeing you don’t get misplaced or confused. The course consists of classes on buffer overflows, bypassing reminiscence safety features like Knowledge Execution Prevention & deploying malicious shellcodes. College students will find out about a wide range of completely different buffer overflow exploits together with SEH-based overflows, which use the Home windows Structured Exception Handler to achieve dependable management over execution. The course additionally covers writing an exploit stager, dealing with giant shellcodes with Winsock-based exploit stagers, and strategies for reusing present sockets to bypass area restrictions.
Superior Methods and Matters
As a part of the curriculum, learners will discover the right way to bypass DEP stack safety utilizing Return Oriented Programming to bypass Knowledge Execution Prevention, using VirtualAlloc & WriteProcessMemory for DEP bypass. Superior exploit strategies embrace:
-
Writing ROP decoders & leveraging pwntools for environment friendly exploit growth
-
Overcoming Deal with Area Structure Randomization with partial RET overwrites
-
Transitioning from Home windows to Linux exploitation by establishing a Linux VM and utilizing gdb for debugging
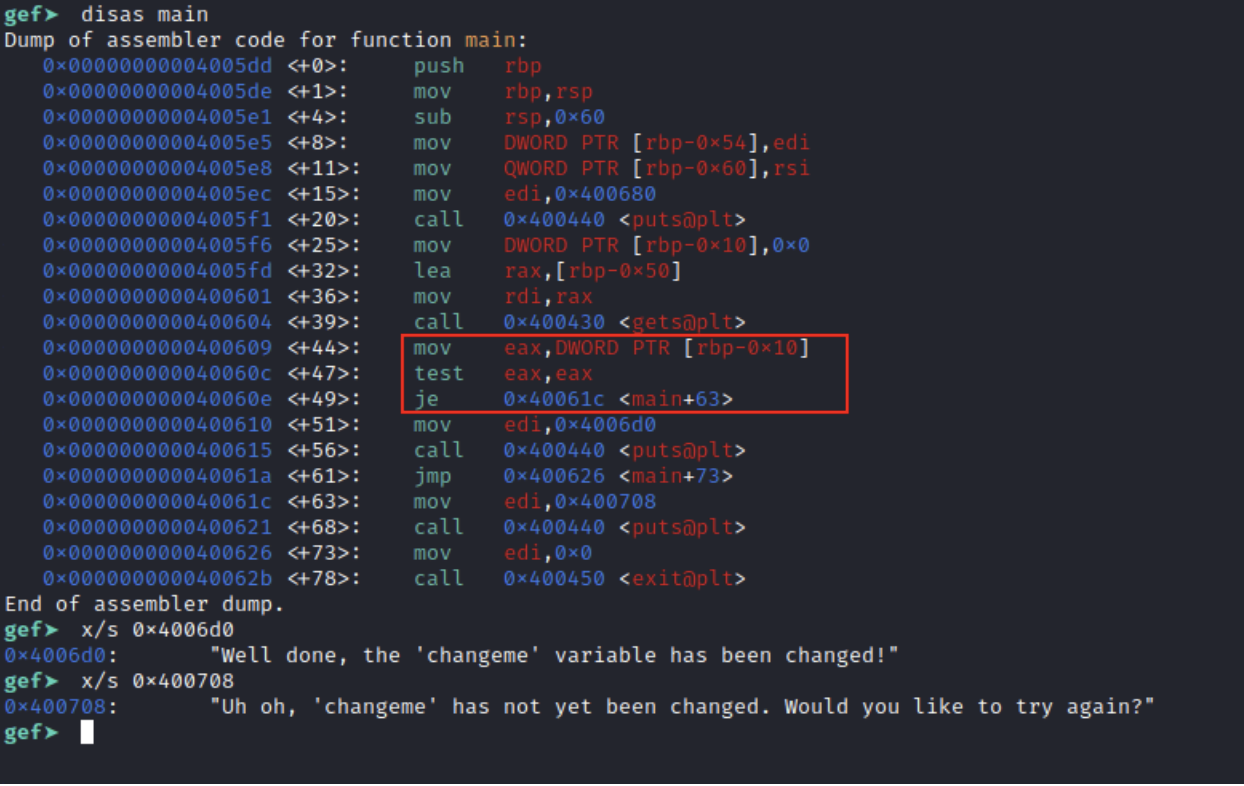
(whereas this screenshot would possibly look complicated now, after following the course you’ll don’t have any downside leaping into meeting code like this)
Specialised Modules
The course additionally introduces college students to egg hunter shellcode, whereas the time period “egg hunter” would possibly sound humorous, this little trick to find shellcode in reminiscence will assist you to deal with inaccessible reminiscence areas to make sure dependable exploitation. Members will study to use use-after-free vulnerabilities to regulate the instruction pointer by understanding heap reminiscence administration and leveraging freed reminiscence for arbitrary code execution.
(authors inventive rendition of a “egg hunter”)
Professional Teacher
The course is led by a seasoned purple group operator whose hacker deal with is Nop, he has in depth expertise in info safety & exploit growth. Having begun his infosec journey by college packages and certifications corresponding to OSCP and OSED, the trainer now focuses on reverse engineering and binary exploitation.
He truly began as a scholar of Guided Hacking in 2020 and later utilized for a job posting to make academic content material for GH, it is a actual success story showcasing the worth of GH. His detailed and fascinating tutorials present his ardour for educating and analysis. He often shares his data at universities and conferences, making him a well-known determine within the cybersecurity group.

(legendary creator of Guided Hacking’s Exploit Dev Course)
Interactive Studying Expertise
Guided Hacking’s Binary Exploit Improvement Course affords a singular mix of video tutorials & written articles. Every module is designed to be each informative and sensible, encouraging hands-on studying. College students are urged to observe the accompanying video tutorials and confer with the written content material as wanted, guaranteeing a well-rounded understanding of every matter. Enroll Immediately
College students can enroll on the Guided Hacking web site to achieve full entry to the Binary Exploit Improvement Course. By changing into a member, learners can view all course content material, obtain unique software program, obtain updates on new modules and tutorials. A Guided Hacking subscription additionally consists of 10 different programs and 1,300 textual content tutorials, so should you ever get misplaced, there’s at all times one other useful resource on the positioning to set you again on the trail.
About Guided Hacking
Guided Hacking is a number one cybersecurity training platform devoted to offering top quality, in depth coaching for rookies and professionals alike. With a deal with sensible expertise and actual world purposes, Guided Hacking’s programs cowl varied subtopics within the reverse engineering area of interest, together with exploit growth, malware evaluation and recreation hacking. It’s really a outstanding useful resource, there are such a lot of tutorials that the proprietor of Guided Hacking says the toughest a part of his job is holding all of it organized. If you wish to checkout a few of their free content material to see what you is perhaps lacking out on, they often publish content material on their YouTube channel.

